This document describes the necessary steps to setup Splunk Cloud for receiving eShare Event logs via a Syslog configuration.
Splunk Server Configuration
HTTP event collector will be configured to receive audit events from eShare to Splunk. The following are instructions to enable the HTTP event collector on Splunk. The eShare events will be sent over HTTPS.
Login to Splunk UI as administrator and go into ‘Settings’ > ‘Data Inputs’
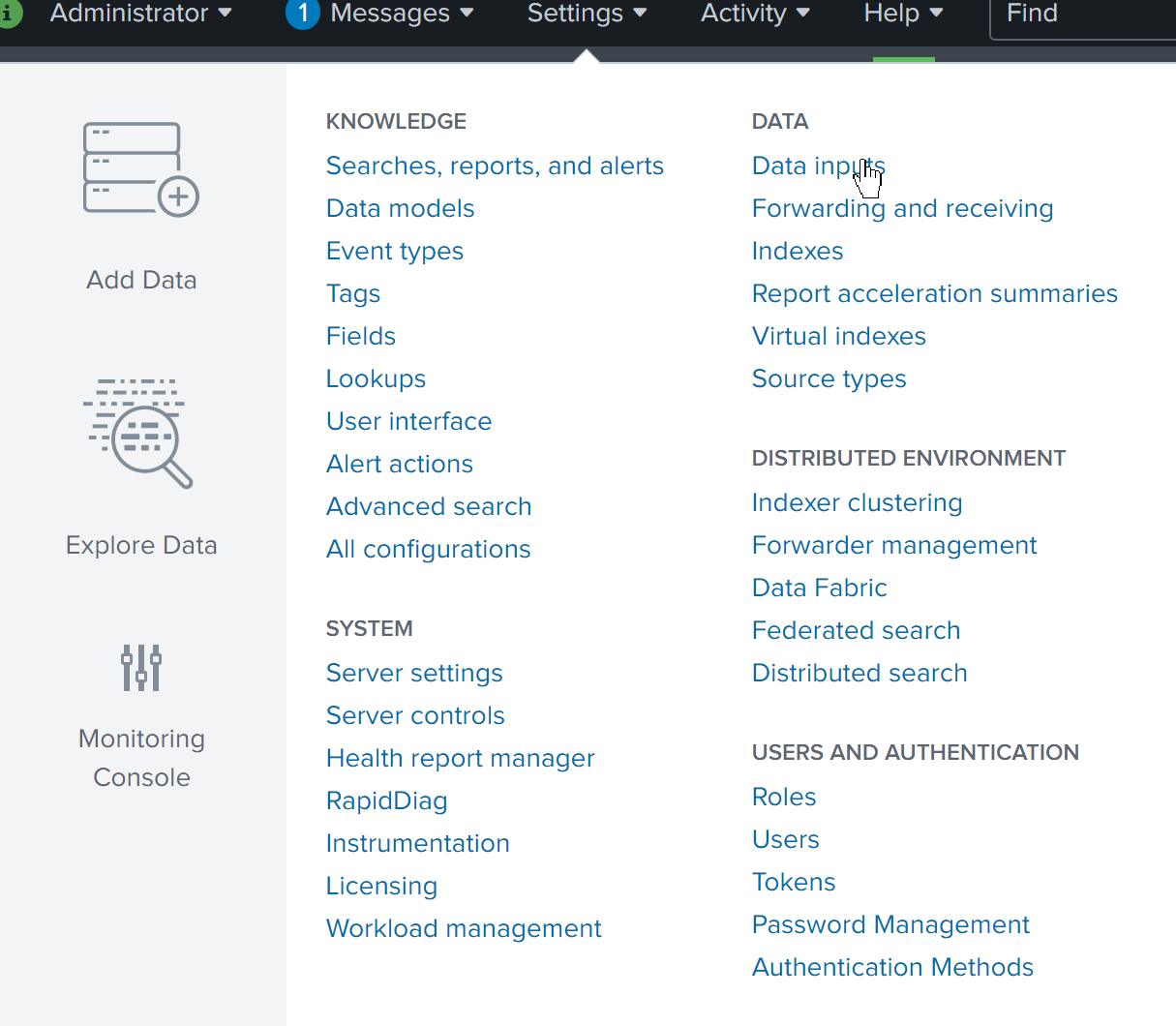
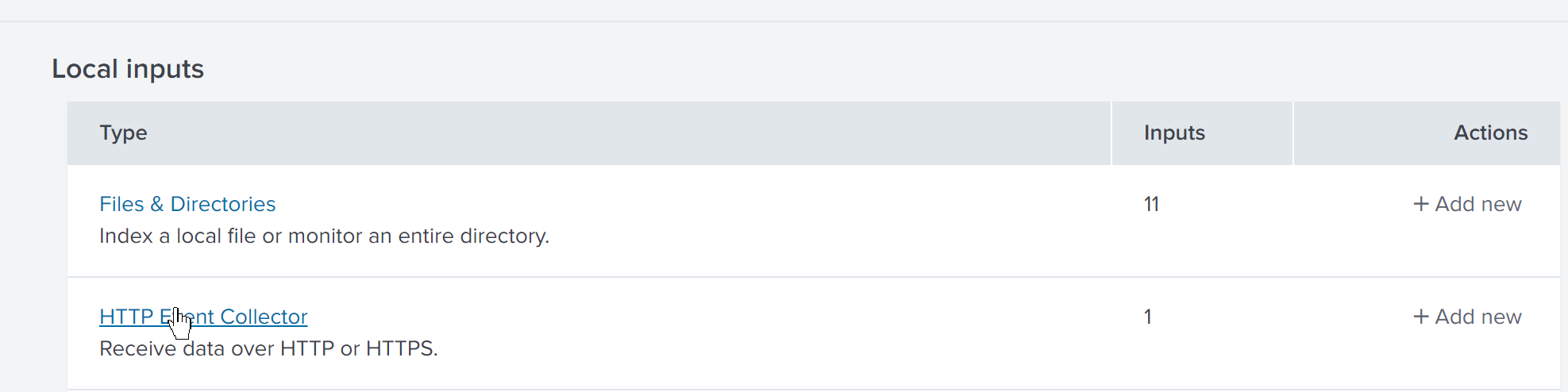
In the Local Inputs section, select ‘HTTP Event Collector’ > ‘Add new’ from the list.
Input a desired ‘Name’ and ‘Description’, the rest may be left at default values.
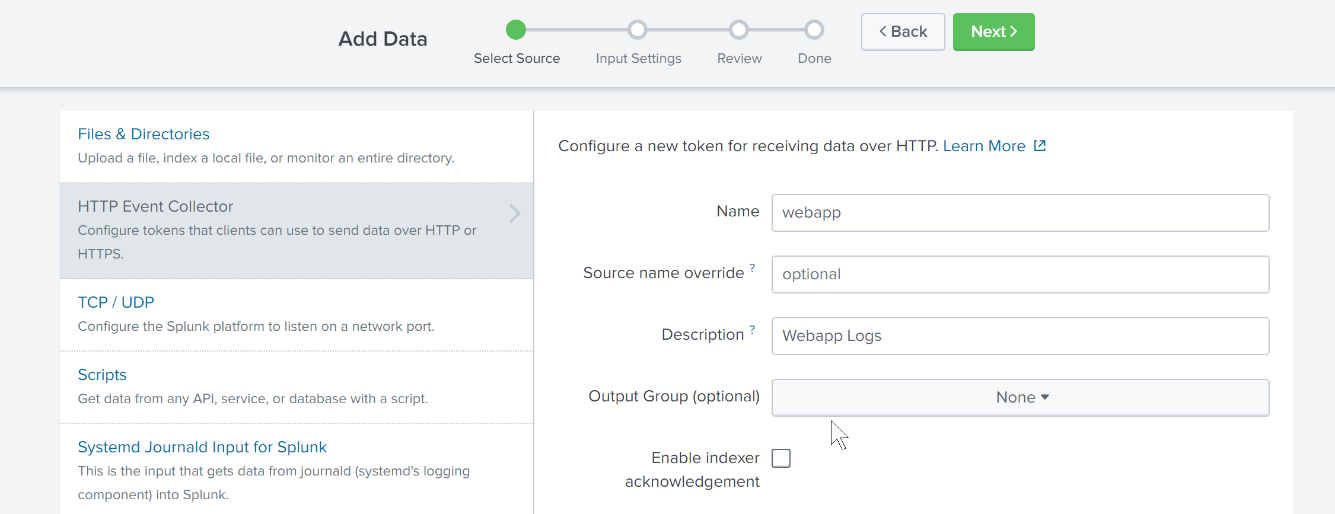
On the Input Settings page, create a new index for webapp logs. ‘Index data type’ should be events, rest of the settings may vary per Splunk deployment.
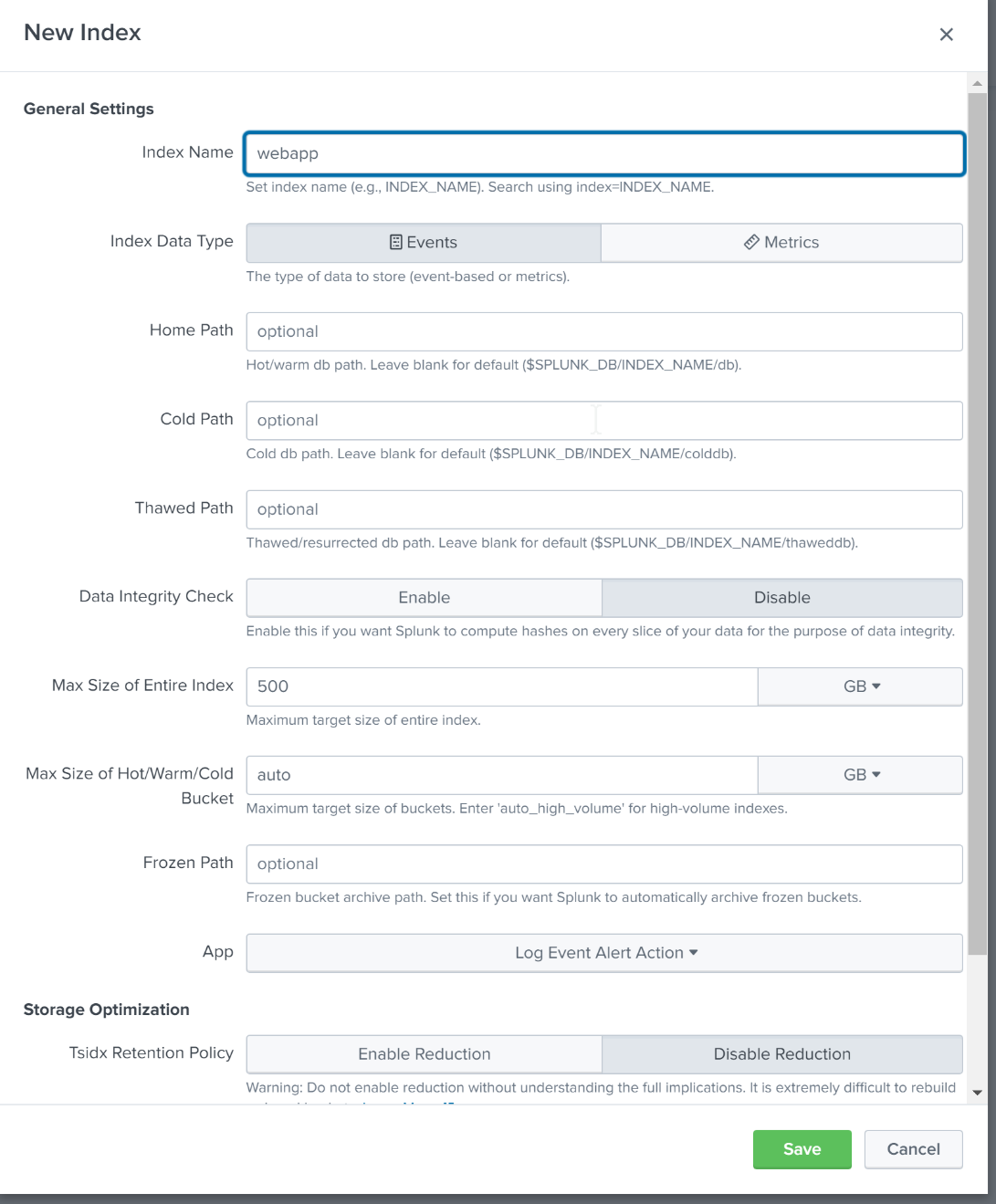
When done, a new Token is created. Please send the generated token to your eShare Customer Success Manager along with the Splunk event collector URL and the public CA certificate if custom certificate is used.
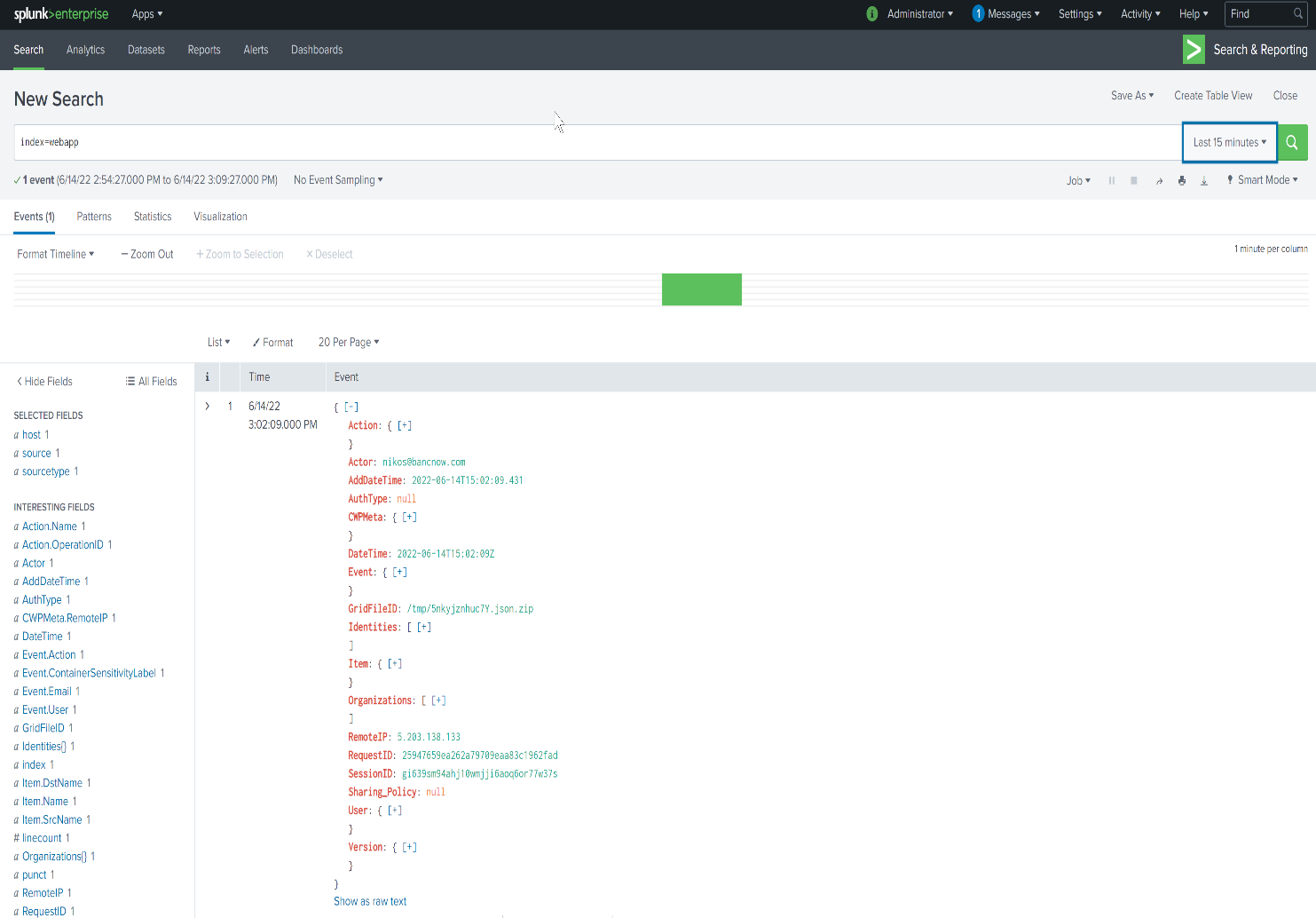
When configuration from eShare side is completed, the Splunk event collector will start receiving logs on the index configured above, example of this can be seen below.