This setup instructions provide information for configuring SAML based sign-in via Okta for all users in the organization to eShare application. The Entity ID and ACS URL, referenced in this document, will be provided to you by eShare’s Customer Success team when the tenant for your organization is provisioned on the eShare platform.
Login to your Okta instance admin portal, typically https://<tenant_name>-admin.okta.com/.
In left navigation pane, expand the ‘Applications’ section and select ‘Applications’ from the menu.
Click on ‘Create App Integration’ button.
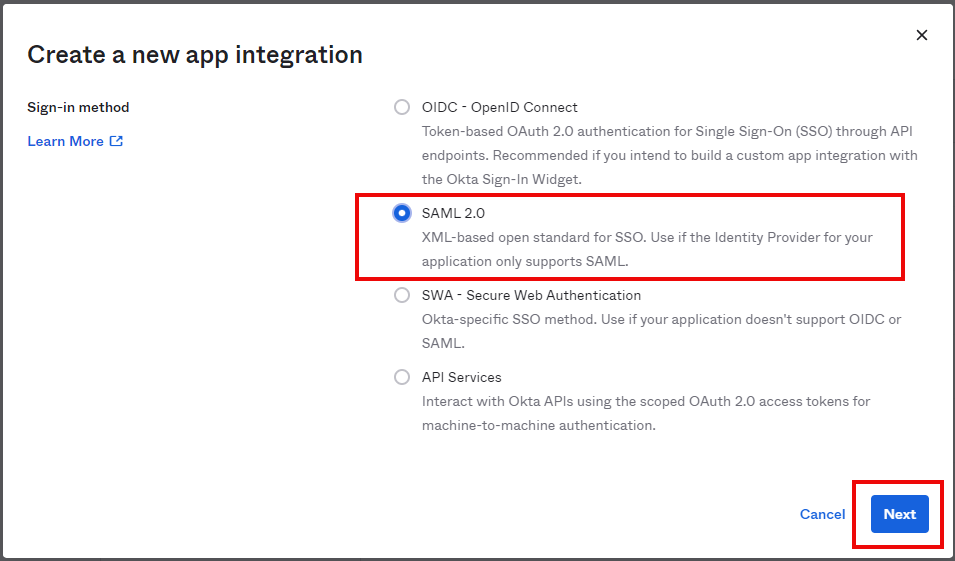
In the ‘Create a new app integration’ pop-up window, select “SAML 2.0” and click ‘Next’.
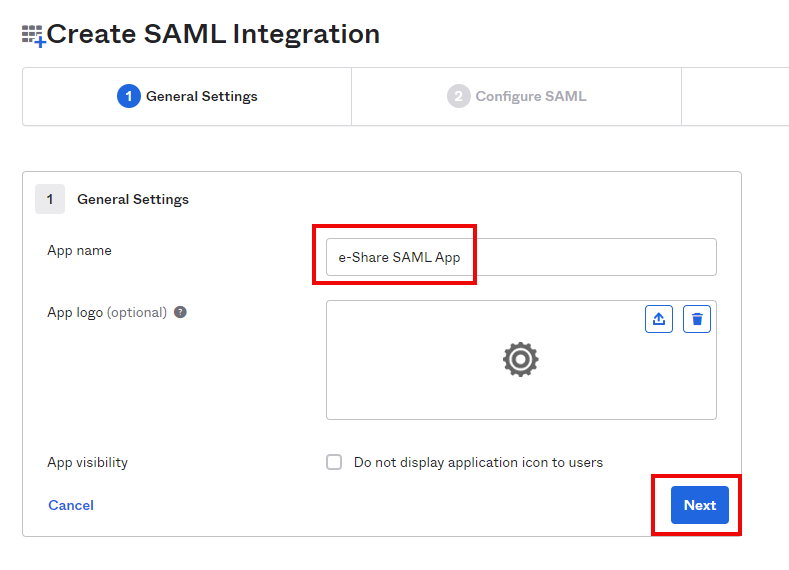
In the ‘Create SAML Integration’ page, under ‘General Settings’ tab, input name of the app (e.g., eShare SAML App) and select ‘Next’.
Witin the ‘Configure SAML’ tab of the same page, for ‘Single sign on URL’ input the ACS URL provided by eShare. For ‘Audience URI (Entity ID)’, input the Entity ID provided by eShare.
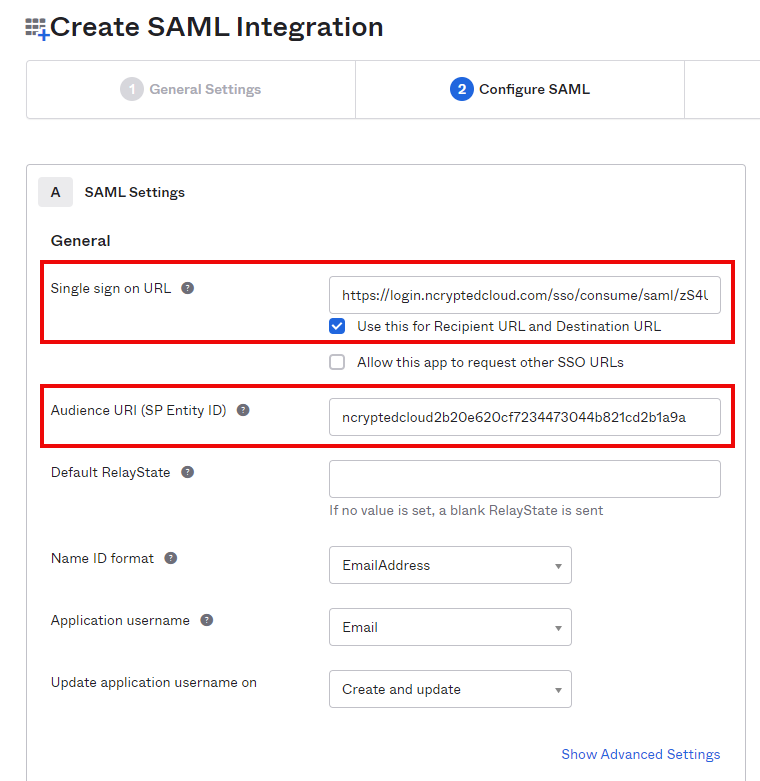
Verify ‘Use this for Recipient URL and Destination URL’ is selected, as shown in the screenshot. Verify values for the following are selected:
Name ID format: EmailAddress
Application username: Email
Update application username on: Create and update
Scroll down to ‘Attributes Statements (optional)’ section. In the displayed statement, input the following:
Name: firstname
Name format: Unspecified – Default value, leave unchanged
Value: From the drop down list, select ‘user.firstName’
Select the ‘Add Another’ button.
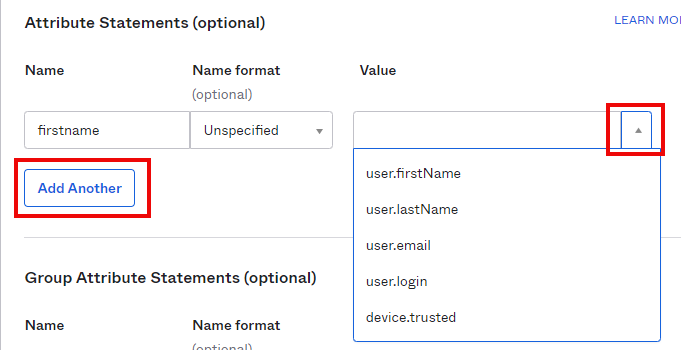
Repeat steps above to add the following statements:
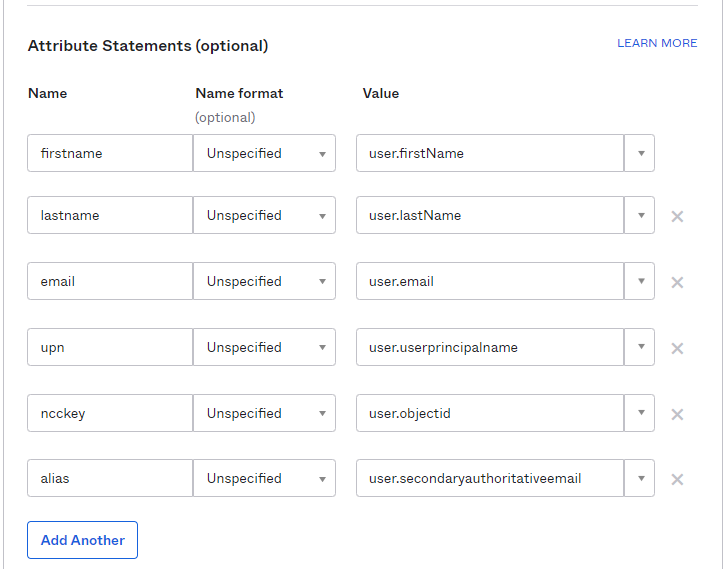
Name: lastname; value: user.lastName
Name: email; value: user.email
Name: upn; value: user.principalname
Name: ncckey; value: user.objectId
Name: alias; value: user.secondaryauthoritativeemail
Note: the ‘user.objectId’ attribute value and ‘alias’ attribute value mappings will may differ depending on which attributes are synched to Okta. Ensure the value mapping selected for ‘ncckey’ is any unique and immutable attribute of the user object, and the value mapping for ‘alias’ contain any alternative email addresses for the user.
A sample of completed ‘Attributes’ section is shown below:
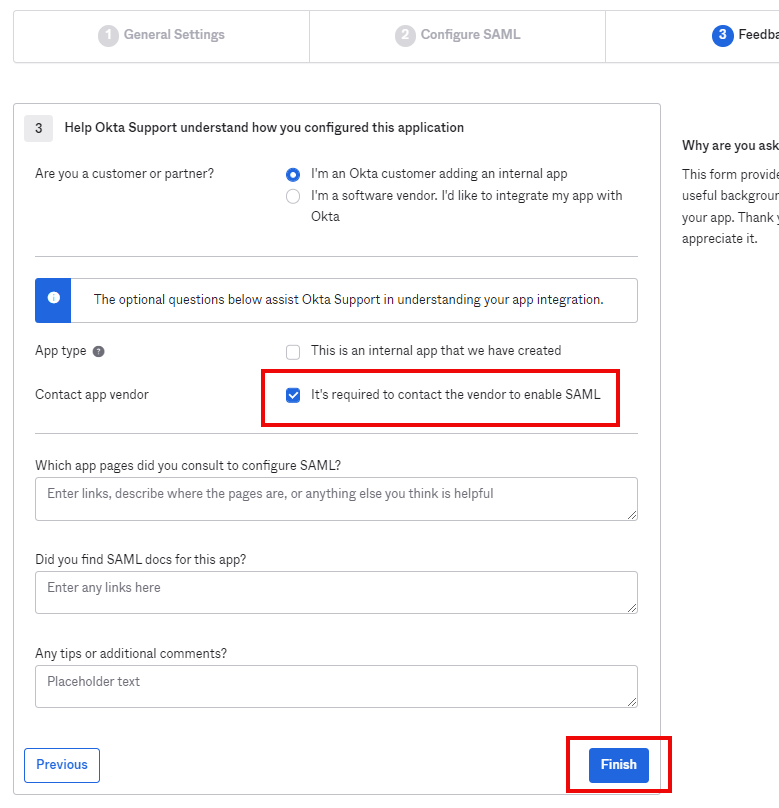
Scroll down and click ‘Next’. In the ‘Feedback’ tab, select ‘I am an Okta customer adding an internal app’ and the ‘It’s required to contact the vendor to enable SAML’ options. When done, click ‘Finish’
Setting tab is displayed. Select the ‘View Setup Instructions’ button to view details.
A new browser tab opens in Okta to ‘How to Configure SAML 2.0 for eShare SAML Application’. Copy and send the following to your eShare Customer Success Manager:
Identity Provider Single Sign-On URL
X.509 Certificate
Alternatively, scroll down to ‘Optional’ section, copy the entire content (XML) and send it to your eShare Customer Success Manager
Switch to the ‘eShare SAML App’ browser tab in Okta Admin Console and navigate to ‘Assignments’ tab for the newly configured app. Add users and/or groups to whom the application should be assigned.
Configure Group Based Entitlement
In situations where only a subset of the authenticated users to eShare application should have the ability to share files/folders from their cloud storage service (e.g., OneDrive, Dropbox, etc.), it is necessary for the Okta to include the Group information of such users.
If users are members of the designated Group, the SAML statement sent by Okta to eShare during the user’s login would include the Group attribute. This allows eShare to consume the Group attribute and enable the cloud storage service. If the Group attribute is not available for the user (because the user is not a member of the Group), such users would be able to access eShare but will only be able to access Trusted Shares received by them.
To configure Okta to include Group attribute in SAML statement:
Login to Okta Admin Console. Switch to ‘Applications‘ > ‘Applications’ > ‘eShare SAML App’ (as configured above).
Select the ‘General’ tab, then the ‘Edit’ button under ‘SAML Settings’ section.
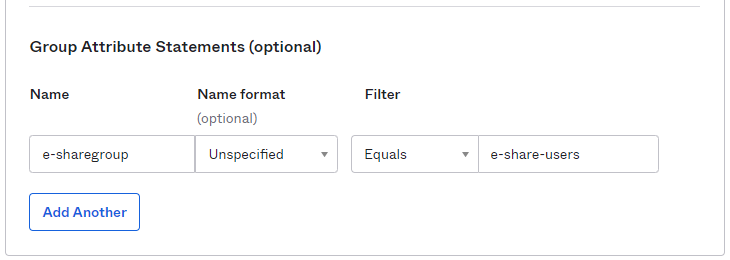
Within the ‘Group Attribute Statements (optional)’ section, input any name for ‘Name’. For ‘Filter’ select ‘Equals’ and input name of the target Group. Members of this group would be provisioned with Cloud Provider in eShare application.
Select ‘Next’ to save the changes.