This document describes the steps to create a custom eShare DLP Tags application in Microsoft Entra (Azure AD) portal. At a high level, the steps involved are:
REQUIREMENT:
The Person performing these steps must have an administrator role assignment of Application Administator, Cloud Application Administator, or Global Administator in the destination M365 tenant.
Application Registration
To register the DLP Tags app for eShare, login to Microsoft Entra console (https://entra.microsoft.com or https://entra.microsoft.us) and navigate to ‘Applications‘ > ‘App Registrations‘.
In ‘App Registrations‘ page, click the ‘+ New registration‘ button in top menu bar.
Input a recognizable unique name for the custom eShare app and select the ‘Register‘ button at bottom of the page.
In a few moments, a shell application is created and ready for further configuration.
Modify Application Manifest - Commercial Cloud
In the newly registered application page, navigate to the ‘Manage‘ > ‘Manifest‘ tab.
In the applications’ manifest, look for ‘requiredResourceAccess‘.
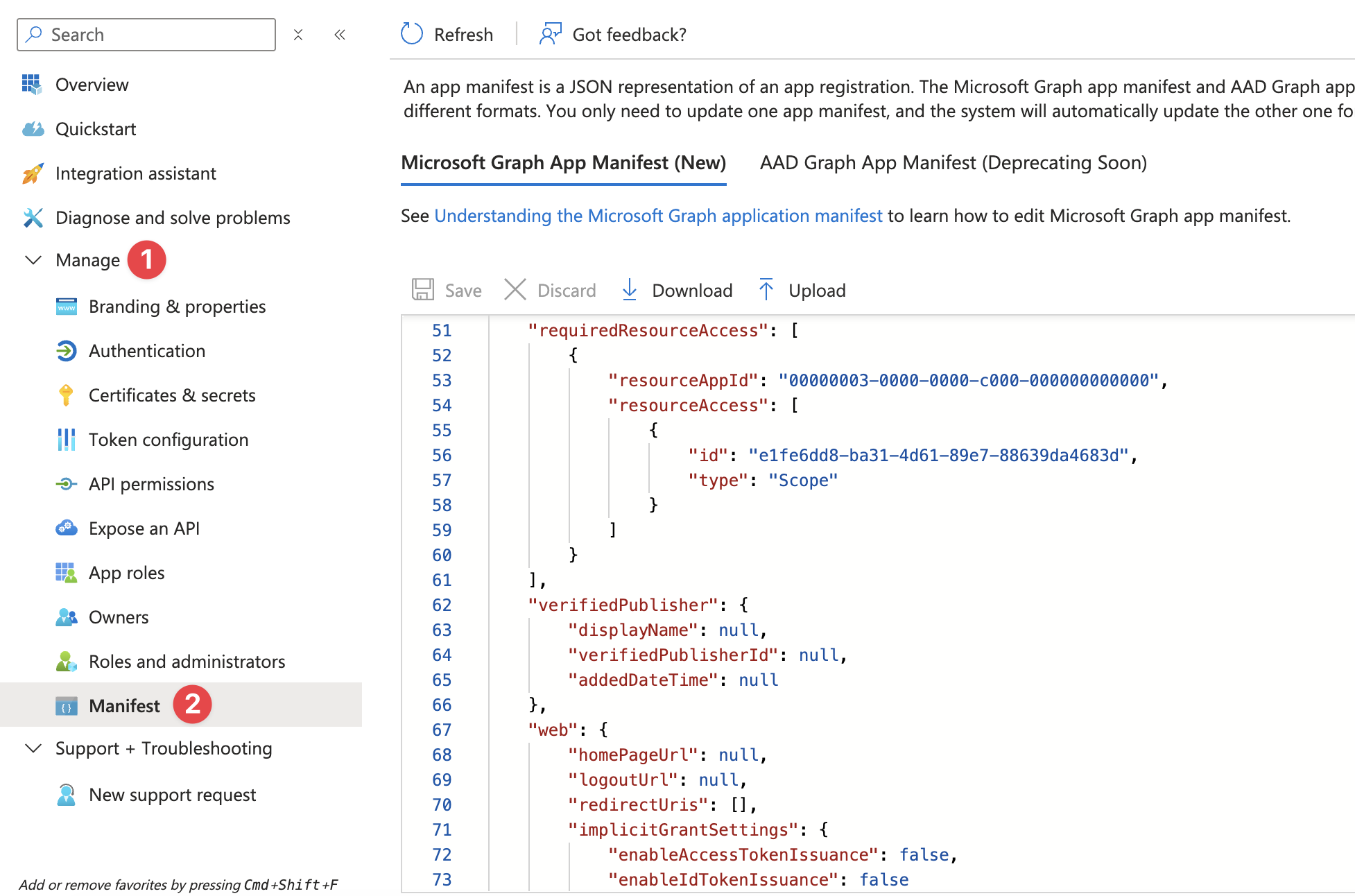
Replace the above string (including the comma at the end) from line 51 to 61 with the below text.
"requiredResourceAccess": [
{
"resourceAppId": "00000003-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "e1fe6dd8-ba31-4d61-89e7-88639da4683d",
"type": "Scope"
}
]
},
{
"resourceAppId": "00000002-0000-0ff1-ce00-000000000000",
"resourceAccess": [
{
"id": "dc50a0fb-09a3-484d-be87-e023b12c6440",
"type": "Role"
}
]
},
{
"resourceAppId": "c5393580-f805-4401-95e8-94b7a6ef2fc2",
"resourceAccess": [
{
"id": "594c1fb6-4f81-4475-ae41-0c394909246c",
"type": "Role"
},
{
"id": "4807a72c-ad38-4250-94c9-4eabfe26cd55",
"type": "Role"
}
]
}
],Click the ‘Save‘ button in top menu bar.
Modify Application Manifest - Government Cloud
In the newly registered application page, navigate to the ‘Manage’ > ‘Manifest’ tab.
In the applications’ manifest, look for ‘requiredResourceAccess’.
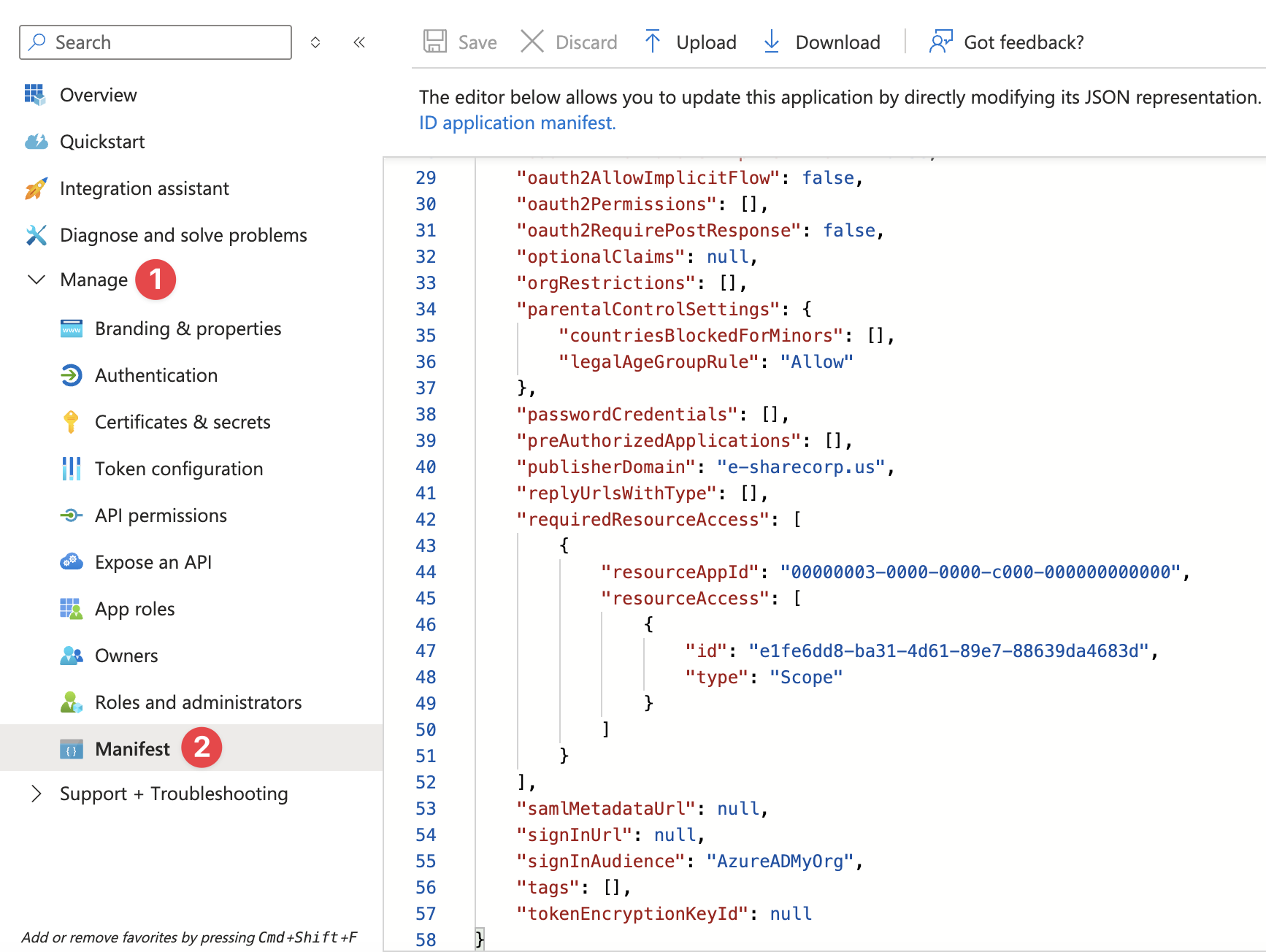
Replace the above string (including the comma at the end) from line 42 to 52 with the below text.
"requiredResourceAccess": [
{
"resourceAppId": "00000003-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "e1fe6dd8-ba31-4d61-89e7-88639da4683d",
"type": "Scope"
}
]
},
{
"resourceAppId": "00000002-0000-0ff1-ce00-000000000000",
"resourceAccess": [
{
"id": "dc50a0fb-09a3-484d-be87-e023b12c6440",
"type": "Role"
}
]
},
{
"resourceAppId": "c5393580-f805-4401-95e8-94b7a6ef2fc2",
"resourceAccess": [
{
"id": "594c1fb6-4f81-4475-ae41-0c394909246c",
"type": "Role"
},
{
"id": "4807a72c-ad38-4250-94c9-4eabfe26cd55",
"type": "Role"
}
]
}
],Click the ‘Save‘ button in top menu bar.
Review API permissions and complete consent
REQUIREMENT:
Granting admin consent for permissions within an app registration must be performed by a Global Administator in the destination M365 tenant.
**Please consult your eShare Customer Success Manager before removing any API Permissions**
For the saved application, navigate to the ‘Manage‘ > ‘API permissions‘ tab.
Select ‘Grant admin consent for <tenant name>‘ in top of the API permissions table
Confirm when prompted.
Provide Security Reader Role Access
In addition to required API permissions, it is required for the Entra ID Application to be assigned the ‘Security Reader’ Privileged role. To do this, navigate to ‘Entra ID’ > ‘Roles & Admins’, assign the Security Reader role, and assign the DLP Tags Application a permanant role assignment.
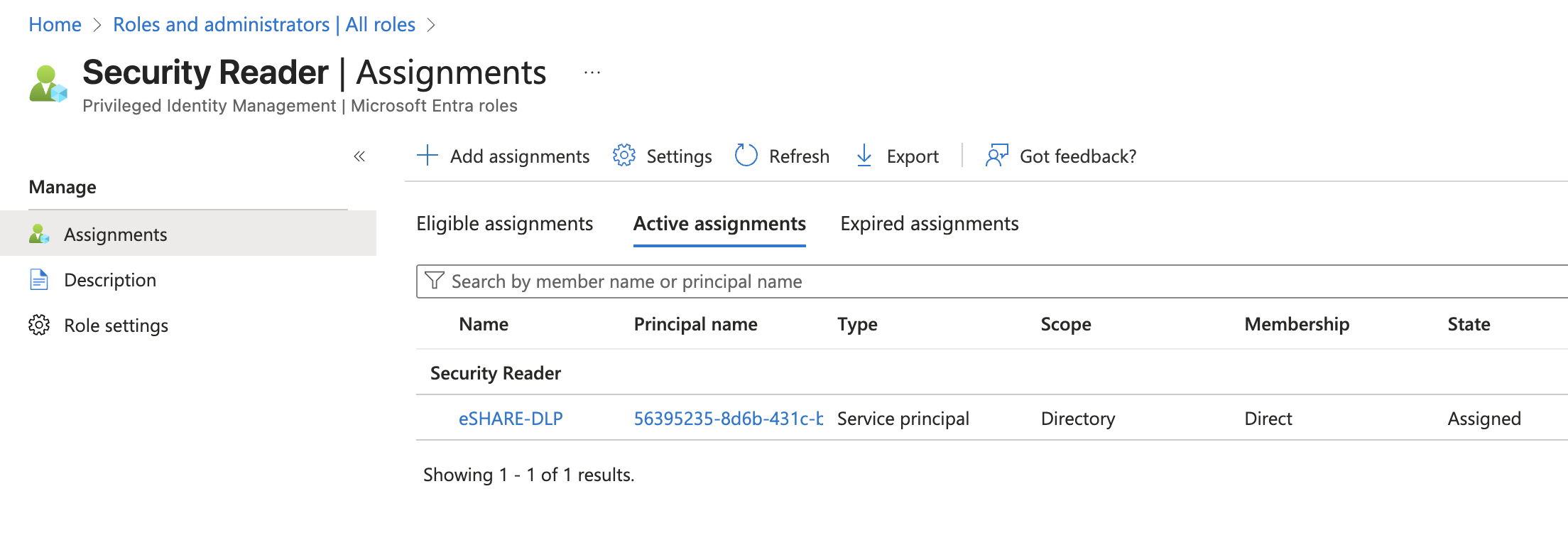
Upload Application Certificate or Client Secret
Option 1: Purchase a certificate from well-known certificate authority, extract the private and public portions of the certificate. Upload the public portion in Azure portal for the application and upload the private key in your eShare admin console (or provide the private key to your eShare admin).
Option 2: Create a self-signed certificate by following instructions available at https://learn.microsoft.com/en-us/azure/active-directory/develop/howto-create-self-signed-certificate.
Option 3: Generate a Client Secret
A short summary of the above instructions for options 1 and 2 are below:
# Create a self-signed certificate in PowerShell
$mycert = "eShareApp"
$mycert = New-SelfSignedCertificate -DnsName "eShareApp" -Subject "CN=eShareApp" -CertStoreLocation "Cert:\CurrentUser\My" -NotAfter (Get-Date).AddYears(50) -KeyExportPolicy Exportable -KeySpec Signature -KeyLength 2048 -KeyAlgorithm RSA -HashAlgorithm SHA256# Extract .key file using OpenSSL
openssl pkcs12 -in eShareApp.pfx -nocerts -nodes -out eShareApp.key# Extract crt from pfx using OpenSSL
openssl pkcs12 -in eShareApp.pfx -clcerts -nokeys -out eShareApp.crt# Export certificate to .pfx file
$mycert | Export-PfxCertificate -FilePath eShareApp.pfx -Password $(ConvertTo-SecureString -String "myp@55W0rd" -AsPlainText -Force)When appropriate certificate portions are available, navigate to ‘Manage‘ > ‘Certificates & secrets’
In ‘Certificates’ tab, click on ‘Upload certificate’ button. Upload the CRT file from the above steps and click on ‘Add’ at bottom of the open pane.
Collect Items Required for eShare DLP Tags Service
M365 Tenant ID: Navigate to ‘Identity > Overview’ tab of the Entra admin console, copy the ‘Tenant ID’ and save it
Application ID: Navigate to ‘Overview’ tab of the application, copy the ‘Application (client) ID’ and save it
Certificate Thumbprint: For the certificate used during application registration process, copy the certificate thumbprint and save it
Private Key: The private key (.key file from above steps) for the certificate uploaded in Entra portal for the application registration.
Client Secret: Only if the organization has opted for this method instead of a certificate, not required if certificate is in use.