This document outlines the high-level steps a new customer needs to take when installing the eSHARE Collaborate product. It also provides the required administrator roles and resources needed to complete the installation. At a high level, the steps involved are:
MySQL or Azure SQL Database for Secure Conversations (Core Product & Secure Mail Module)
Azure Storage Account for Inline Images (Core Product & Secure Mail Module)
Native eSHARE M365 Trusted Sharing Action Menu App (Core Product)
.png)
DNS Entries (Core Product)
Prerequisites: An administrator who has access and can manage the DNS entries of the company domain.
How to Install: DNS Entries will be provided by your eSHARE Customer Success manager
What is Required: DNS entries will need to be entered into for the Company Domain
Why is this needed: They are required for the following reasons:
a CNAME entry is required for the secure web portal where users can manage their Trusted shares e.g. secure.DOMAIN.com.
a CNAME entry is required for the ShareWithMe Link e.g. sendto.DOMAIN.com
2 SPF TXT records are required for Branded email notifications and delivery.
An optional CNAME entry email tracking.
DMARC – update to include records for email notifications
DKIM – update to include records for email notifications
Single Sign-On Integration: SAML2 (Core Product)
Prerequisites: An administrator with the M365 Global Administrator Role or Application Administrator Role.
How to Install: Single Sign-On (SSO) Configuration
What is Required: Administrator will create an eSHARE SAML Application in Azure Active Directory Enterprise Applications using instructions provided by the eSHARE Customer Success Team
Why is this needed: Creating a Single Sign-On Application will allow users to seamlessly login to the eSHARE Secure web portal using the organization’s IdP provider and removes the need to create a separate username and password. It is more secure and allows administrators to manage a single identity.
Aside from Microsoft Entra ID, eSHARE also integrates seamlessly with Single Sign-On (SSO) solutions leveraging federated identity providers (IdPs) such as Okta, PingID, and other standards-based providers.
App Registration in Microsoft Entra ID (Core Product)
Prerequisites: An administrator with the M365 Global Administrator Role, and an eSHARE Administrator.
How to Install: Create eShare Entra ID App Registration
What is Required: M365 Administrator will create an App Registration in Entra ID, providing the App specific API permissions which allows eSHARE to integrate with OneDrive, SharePoint, Teams, and Sensitivity labels. A Certificate and Private Key pair is also needed for the eSHARE Application to authenticate with the created Service Principal.
Why is this needed: Creating the eSHARE app registration and consenting to specific GRAPH API permissions (see below for specifics on API Permissions) creates the eSHARE Service Principal in the Organization’s M365 Enterprise Application, and provides access to the Cloud Providers (OneDrive, SharePoint, and Teams). This will allow users in your organization to Share Data in their OneDrive, SharePoint, and Teams through the eSHARE application. Additionally, it creates a link to the organizations defined Sensitivity Labels, allowing the ability to map the labels to Sharing policies enabling active controls when sharing sensitive data.
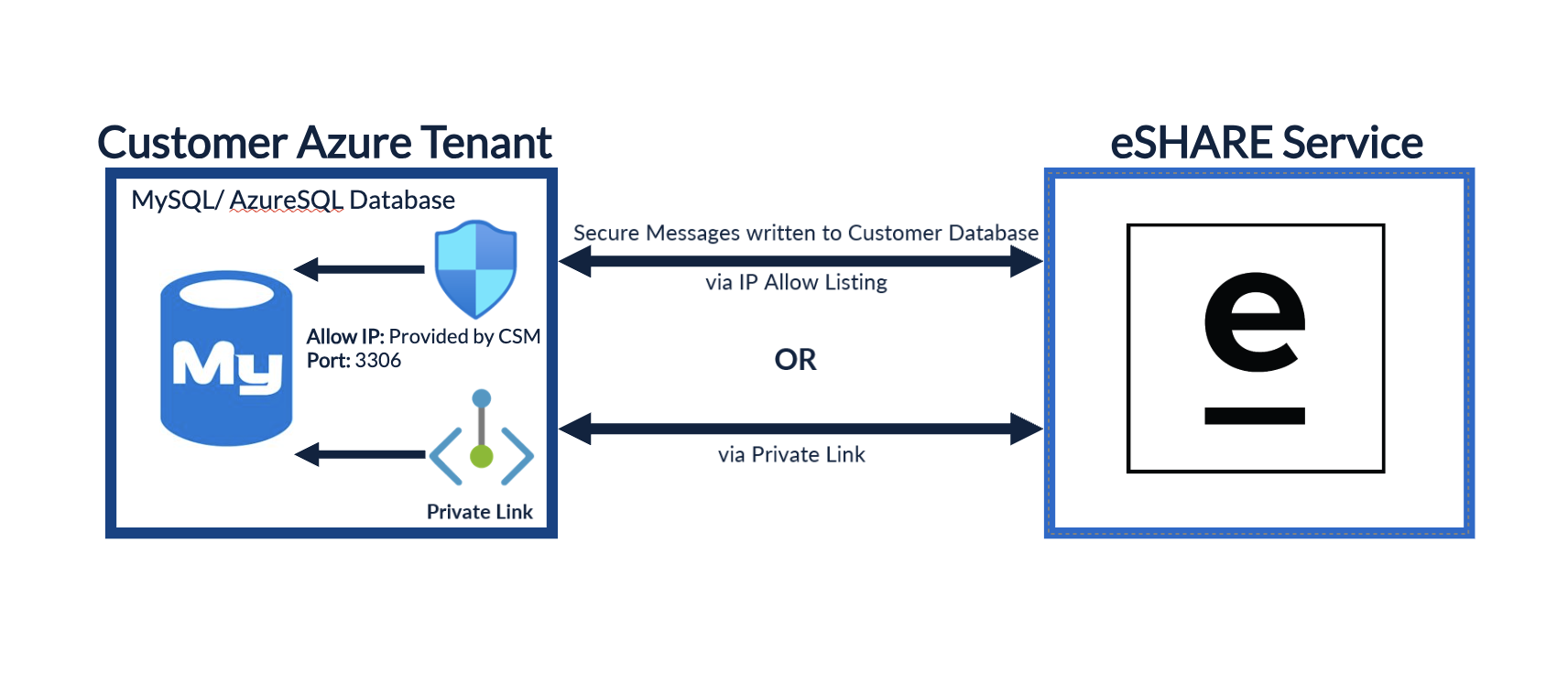
MySQL or Azure SQL Database for Secure Conversations (Core Product & Secure Mail Module)
Prerequisites: An administrator with Azure Subscription Owner Role or Contributor Role, and an eSHARE Administrator.
How to Install: MySQL Database for Secure Messages or Azure SQL Database for Secure Messages
What is Required: Administrator will create a MySQL or Azure SQL database in Azure that will store the text from secure conversations. The eSHARE admin will then enter the database information into the eSHARE admin console to complete the connection.
Why is this needed: Creating the MySQL or Azure SQL Database allows the organization to store all Secure Conversations that occur in Trusted Shares within their own environment. This allows the organization to store their own data in their environment instead of storing it in eSHARE’s database.
Azure Storage Account for Inline Images (Core Product & Secure Mail Module)
Prerequisites: An administrator with Azure Subscription Owner Role or Contributor Role, and an eSHARE Administrator.
How to Install: Adding Azure Blob Storage Account for Images
What is Required: Administrator will create an Azure Blob Storage Account that will store inline images that are sent through a secured email or within secure conversations. The eSHARE admin will then enter the storage information into the eSHARE admin console to complete the connection.
Why is this needed: Creating the Azure Blob Storage Account allows the organization to store/host all inline images that are sent through a secured email or through secure conversations within their own environment. If there is no storage account linked to the organization’s eSHARE tenant, inline images will not be uploaded into the secure conversations.
Native eSHARE Trusted Sharing M365 App (Core Product)
Prerequisites: An administrator with M365 Global Administrator Role or SharePoint & Teams Administrator Role
How to Install: M365 Application Installation Guide
What is Required: Administrator will install the eSHARE Trusted Sharing application from the M365 SharePoint store and will provide consent to the needed Graph API Access within SharePoint Admin page.
Why is this needed: The eSHARE Trusted Sharing Applications allows users within the organization to create and manage Trusted Shares natively within a Teams, SharePoint, Outlook, and the Office Homepage. It creates a better user experience by removing the need to use the Cloud Web Portal to share files and removes the burden of needing to register Teams/SharePoint Sites in the eSHARE Admin Console.
Native eSHARE M365 Trusted Sharing Action Menu App (Core Product)
NOTE:
If installed, the app will appear org-wide within OneDrive, SharePoint, and Teams, can be considered optional but it is still recommended to install.
Prerequisites: An administrator with Global Administrator Role
How to Install: External Share Action Menu App Installation Guide
What is Required: Administrator will install the eSHARE Action Menu app as an Enterprise Application and will provide consent to the needed Graph API Access.
Why is this needed: The M365 Trusted Sharing Action Menu allows users to create Trusted Shares from the action menus that M365 presents to users when a file or folder is selected from within Teams, SharePoint Online, and OneDrive. Users enjoy all the benefits of external file sharing using eSHARE while never leaving M365. This greatly improves user productivity and dramatically reduces the need for change management and training.
Exchange Mail Connectors (Secure Mail Module)
Prerequisites: An administrator with M365 Global Administrator Role or Exchange Administrator Role.
How to Install: Install Secure Collaboration Gateway
What is Required: Administrator will create an Inbound Connector and an Outbound Connector that will route mail to the eSHARE Secure Mail Gateway.
Why is this needed: To utilize the Secure Mail Gateway feature, these connectors must be created so mail outgoing mail is routed to the SMG Appliance and can be properly secured based on the classification the email was given. The Appliance will also need to send confirmation or bounce emails for any outgoing mail that was sent.
Client Infrastructure - Customer Specific
In some cases an organization may have network appliances (CASB, IDS, Firewall, proxy, etc.) that may block access to eSHARE service URLs. Ensure that the following URLs are on the organization’s allow list.
For Commercial tenants:
*.n11d.com
email.DOMAIN.com (subdomain may be different)
secure.DOMAIN.com (subdomain may be different)
sendto.DOMAIN.com (subdomain may be different)
For Government tenants:
email.DOMAIN.com (subdomain may be different)
secure.DOMAIN.com (subdomain may be different)
sendto.DOMAIN.com (subdomain may be different)
Required API Permissions
eSHARE Solution | eSHARE feature | API category | API permission | Type | Granted through | eSHARE explanation for the Permission |
|---|---|---|---|---|---|---|
eSHARE Collaborate | Microsoft Sensitivity Labels | Azure Rights Management Services | Content.DelegatedReader | Application | Admin Consent | Allows eSHARE to read protected content on behalf of a user |
eSHARE Collaborate | Microsoft Sensitivity Labels | Azure Rights Management Services | user_impersonation | Delegated | User consent | Allows eSHARE to use Azure Rights Management feature to access protected content for users |
eSHARE Collaborate | Microsoft Sensitivity Labels | Microsoft Information Protection Sync Service | UnifiedPolicy.User.Read | Delegated | User consent | Allows eSHARE to read all unified policies a user has access to. |
eSHARE Collaborate | OneDrive/SharePoint | Microsoft Graph | Directory.Read.All | Application | Admin consent | Allows eSHARE to read data in your organization's directory, such as users, groups and apps. |
eSHARE Collaborate | OneDrive/SharePoint | Microsoft Graph | Files.ReadWrite.All | Application | Admin consent | Allows eSHARE to read, create, update and delete all files in all site collections without a signed in user. |
eSHARE Collaborate | OneDrive/SharePoint | Microsoft Graph | Group.Read.All | Application | Admin consent | Allows eSHARE to list groups, and to read their properties and all group memberships on behalf of the signed-in user. |
eSHARE Collaborate | OneDrive/SharePoint | Microsoft Graph | GroupMember.Read.All | Application | Admin consent | Allows eSHARE to list groups, read basic group properties and read membership of all groups the signed-in user has access to. |
eSHARE Collaborate | OneDrive/SharePoint | Microsoft Graph | Sites.ReadWrite.All | Application | Admin consent | Allows eSHARE to create, read, update, and delete documents and list items in all site collections without a signed in user. |
eSHARE Collaborate | User Identity | Microsoft Graph | User.Read.All | Application | Admin consent | Allows eSHARE to read the full set of profile properties, reports, and managers of other users in your organization, on behalf of the signed-in user. |
eSHARE Collaborate | Shared Mailbox & Microsoft Purview DLP | Office 365 Exchange Online | Exchange.ManageAsApp | Application | Admin consent | Allows eSHARE to manage the organization's Exchange environment without any user interaction. This includes mailboxes, groups, and other configuration objects. |
eSHARE Collaborate | Microsoft Purview DLP | Office 365 Management APIs | ActivityFeed.Read | Application | Admin consent | Allows eSHARE to read activity data for your organization. |
eSHARE Collaborate | Microsoft Purview DLP | Office 365 Management APIs | ActivityFeed.ReadDlp | Application | Admin consent | Allows eSHARE to read DLP policy events, including detected sensitive data, for your organization. |
eSHARE Collaborate | SharePoint Search & Microsoft Sensitivity Labels | SharePoint | Sites.Read.All | Application | Admin consent | Allows eSHARE to read documents and list items in all site collections without a signed in user. |